How to maximize Cloudflare security rules
Published on August 24th 2025
Cloudflare offers many powerful features on its free plan, but you are limited to only five custom Security Rules. This tutorial will demonstrate how to maximize those five rules for optimal protection against common threats.
With custom security rules, you can protect your website from malicious bots and crawlers, restrict access to specific IP addresses, implement geo-blocking, and much more.
I have created five rules that provide a strong security baseline:
- IP Blocks
- IP Restricted Hostnames
- IP Auth Routes Restricted
- Bots and Crawlers Block
- Geo Restricted Hostnames
I will go over how each one works and how it can be configured. Once you see these examples, you can then modify and extend these rules further or make them more granular.
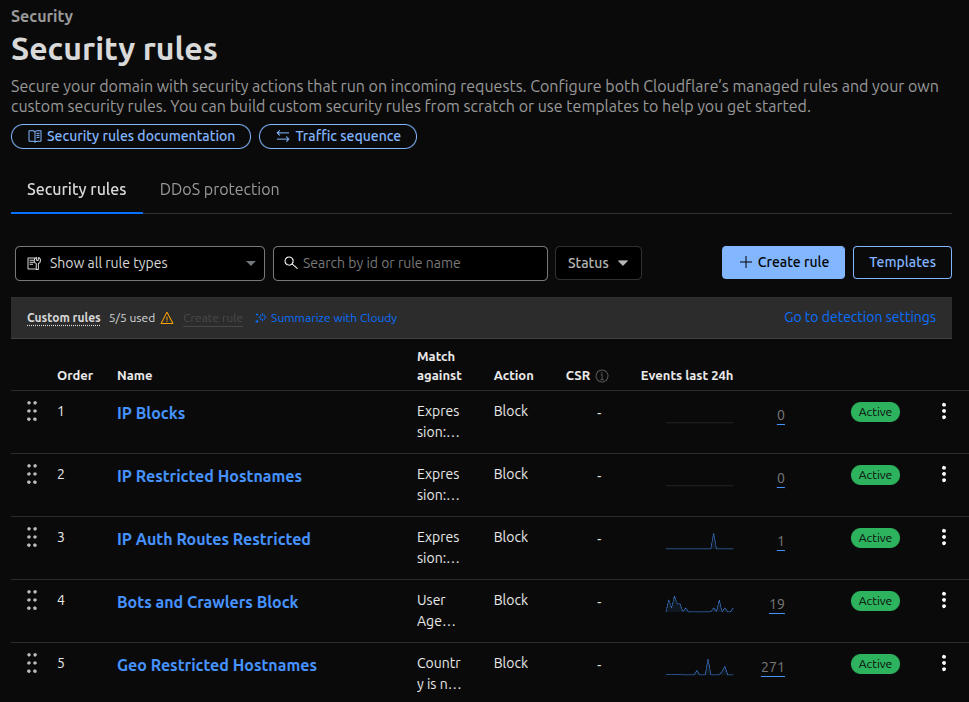
IP Blocks
The IP Blocks rule lets you block specific IP addresses from accessing your domain and subdomains. This is useful if you identify a malicious IP address, perhaps from your Cloudflare web traffic analytics.
To create this rule, set the "Rule name" to "IP Blocks".
For the condition "When incoming requests match...", set the "Field" to "IP Source Address" and the "Operator" to "is in". You can then manually add IP addresses to the "Value" text area.
For the action, set "Then take action..." to "Block".
The "Place at" option should be set to "First". Security rules execute in the order you set them, and we want to check for blocked IPs immediately.
Finally, save the rule.
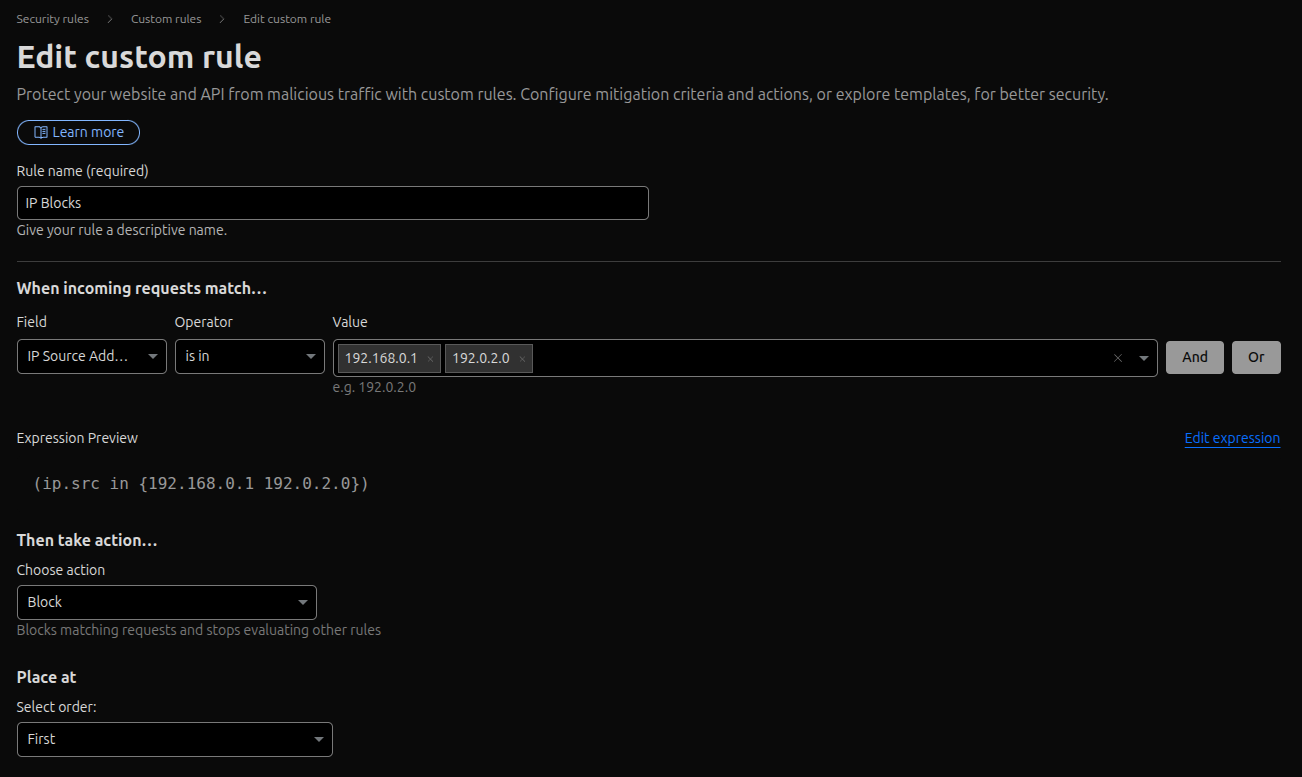
IP Restricted Hostnames
This rule allows you to restrict entire domains or subdomains to a list of allowed IP addresses. This is ideal for protecting a staging website during development or an admin panel that only a few users should access.
Set the "Rule name" to "IP Restricted Hostnames".
For the condition "When incoming requests match...", create two expressions joined by "And":
- Set the first expression's "Field" to "IP Source Address" and "Operator" to "is not in". The "Value" should be your list of allowed IP addresses.
- Set the second expression's "Field" to "Hostname" and "Operator" to "is in". The "Value" should be the hostnames you want to protect.
This logic blocks any request that is not from an allowed IP and is for one of the specified hostnames.
Set "Then take action..." to "Block".
"Place at" can be set to "Custom" to position it correctly in your rule list.
Save the rule.
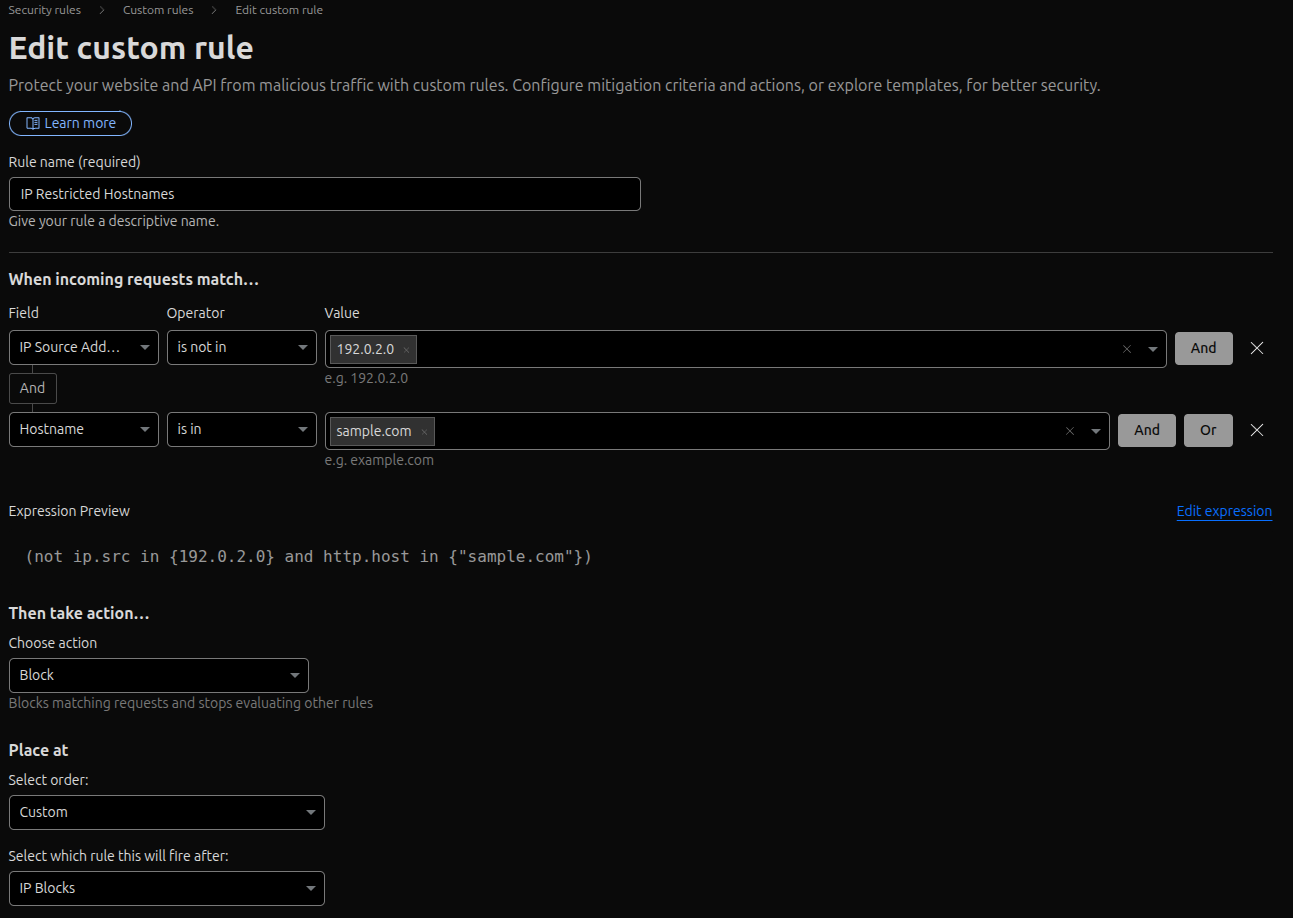
IP Auth Routes Restricted
This rule extends the previous concept to restrict specific URL paths, such as `/admin/`, `/login`, or `/wp-admin`, to certain IP addresses.
Set the "Rule name" to "IP Auth Routes Restricted".
For "When incoming requests match...", you will create three conditions joined by "And":
- IP Source Address `is not in` [Your Allowed IPs]
- Hostname `is in` [Your Hostnames]
- URI Path `is in` ["/admin/", "/login", "/wp-admin"]
The screenshot below shows the web routes that I restrict as an example.
This rule blocks any request that is not from an allowed IP and is for a protected hostname and matches one of the sensitive URI paths.
Set "Then take action..." to "Block".
"Place at" should be set as "Custom".
Save the rule.
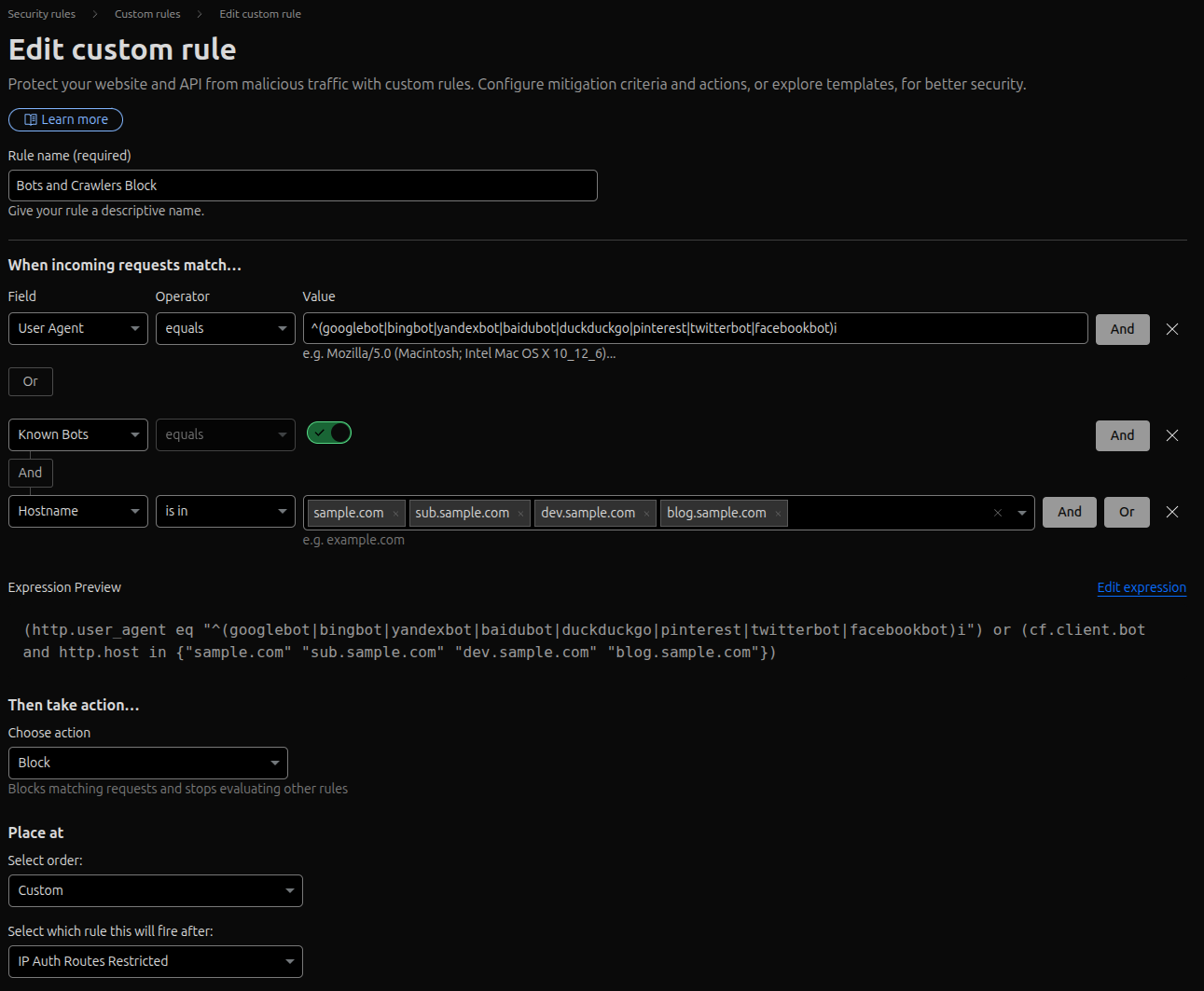
Bots and Crawlers Block
This rule blocks known search engine crawlers and other bots from accessing specific domains or subdomains. This can be useful for staging sites or private applications that you don't want indexed or scanned.
Set the "Rule name" to "Bots and Crawlers Block".
The logic for this rule is: `(User Agent matches a crawler OR the request is from a Known Bot) AND the Hostname is one you want to protect`.
To build this, you'll need to use the expression editor to group the "Or" conditions.
- In the first part of the group, set "Field" to "User Agent" and "Operator" to "equals". The "Value" should be this regular expression:
^(googlebot|bingbot|yandexbot|baidubot|duckduckgo|pinterest|twitterbot|facebookbot)i - Click "Or".
- In the second part of the group, set "Field" to "Known Bots" and "Operator" to "equals". Enable this by clicking the toggle switch. "Known Bots" is a managed list provided by Cloudflare.
- Now, add an "And" condition outside the group. Set its "Field" to "Hostname" and "Operator" to "is in". The "Value" can be one or more hostnames/subdomains.
Set "Then take action..." to "Block".
"Place at" should be set as "Custom".
Save the rule.
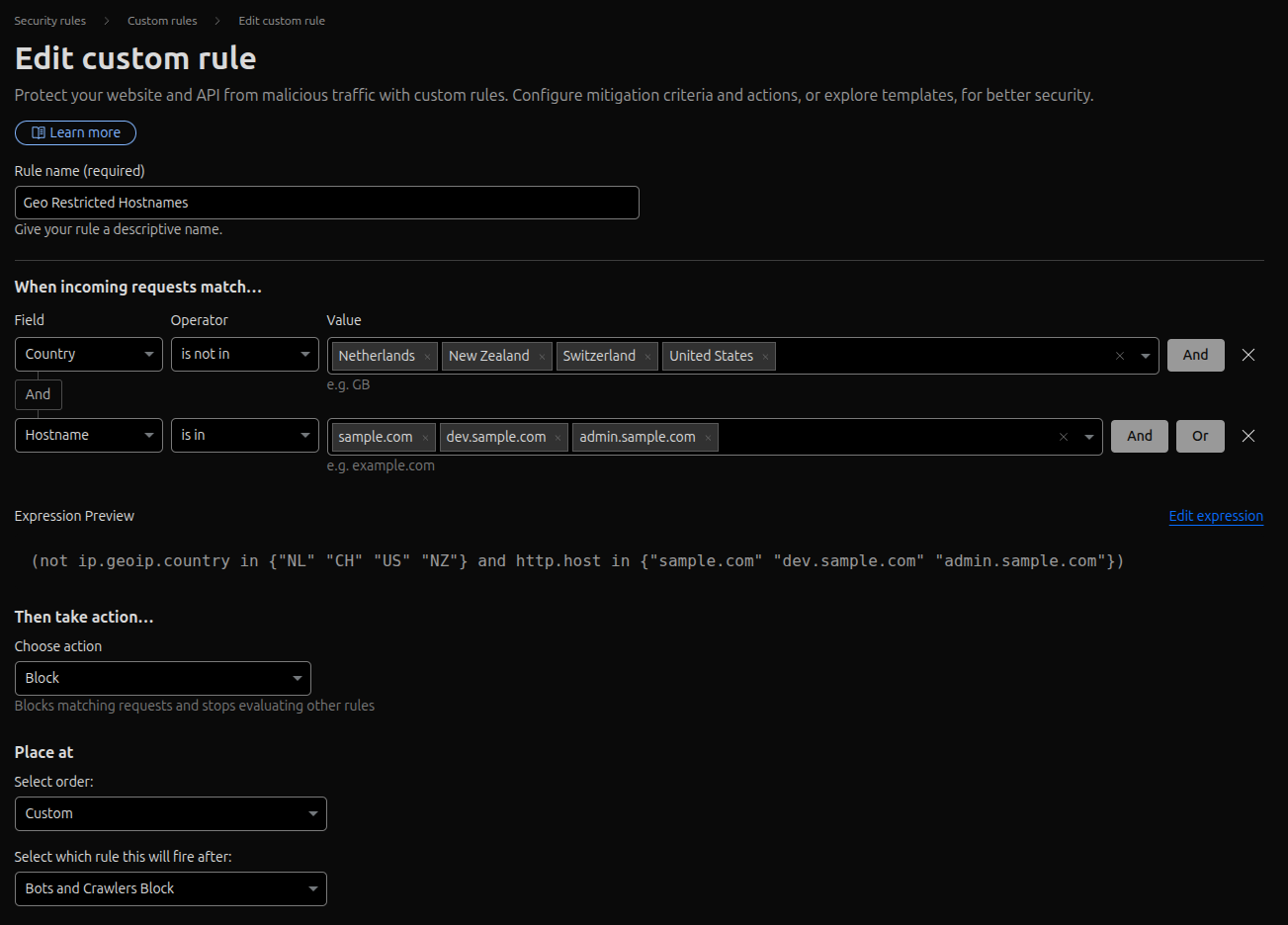
Geo Restricted Hostnames
This rule restricts access to your domains or subdomains based on the visitor's country. It's particularly useful if your service is only intended for specific geographic regions.
Set the "Rule name" to "Geo Restricted Hostnames".
For "When incoming requests match...", create two conditions joined by "And":
- Set the first expression's "Field" to "Country" and "Operator" to "is not in". For the "Value", select the countries you want to allow access from.
- Set the second expression's "Field" to "Hostname" and "Operator" to "is in". The "Value" should be the hostnames you want to protect.
This rule blocks any request that is not from an allowed country and is for one of the specified hostnames.
Set "Then take action..." to "Block".
"Place at" should be set as "Custom".
Save the rule.
With these five security rules as a foundation, you have a flexible and powerful setup for protecting your websites. Feel free to modify these examples and tailor them to your specific needs.